MagpieCTF 2023 - What is Password
This challenge had us look at a pcap file and look through the web traffic. The file can be found here.
Solution
First we open the file in Wireshark.
Since the amount of web traffic is very small we can just analyze it manually. Notice the HTTP GET request for /Password.PNG in frame 4. After nearly 10 ACKs and PSHs, we get our server response code 200, HTTP OK in frame 15. Note, alternatively you could filter through the HTTP protocol just to see the HTTP traffic.
Opening frame 15 we enter the HTTP layer and expand the fields until we see the Portable Network Graphics field. Right click and export the packet bytes and give it a name.png.
Opening the image we see the flag:
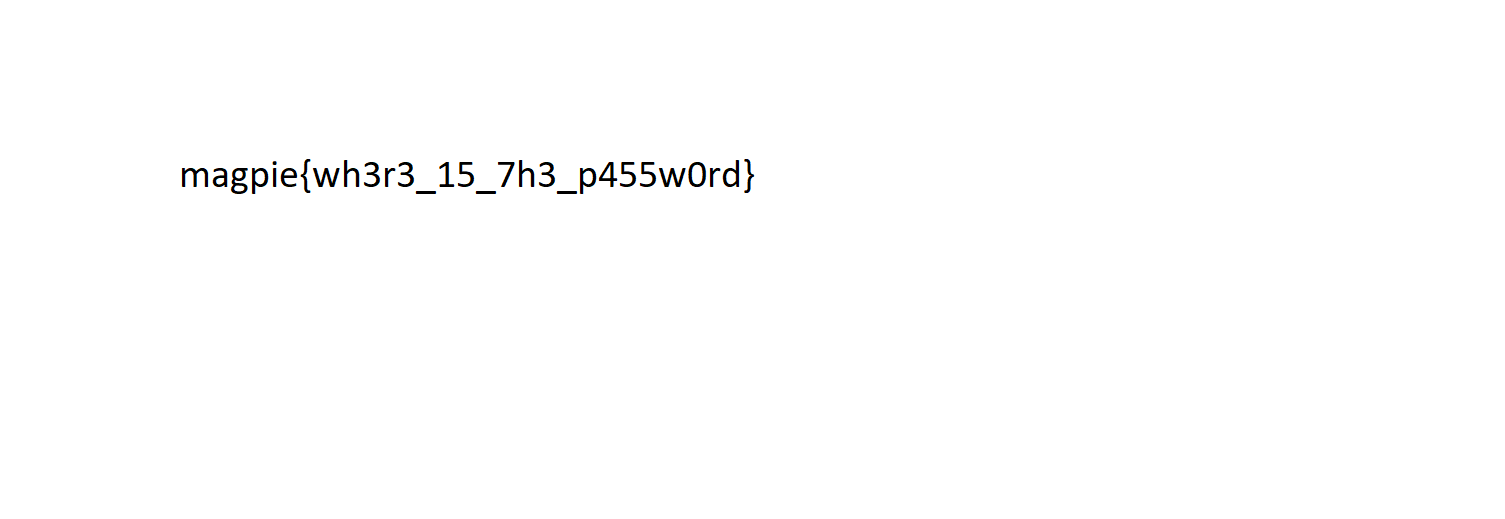
magpie{wh3r3_15_7h3_p455w0rd}
Read other posts