MagpieCTF 2023 - No Password Here
This challenge had us look at a C source code file and try to find a way to cause a buffer overflow. Here is the compiled program and its lib.
Solution
Opening the C file, we see that the file does not have the typical gets function that is well known for its vulnerabilities. Instead the function we have to focus on it scanf. If you aren’t aware, scanf does not have bound checking capability so if the input string is longer than the buffer size, then it will overflow.
Let’s test that out by making a quick test flag.txt in the same directory as the Code executable. Now we will pass some arbirtuary input like:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
We see the output below:
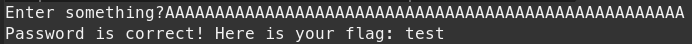
The flag is:
magpie{5c4nf_n07_54f3}
Read other posts